“As a result of they function at this essential boundary, they usually maintain elevated privileges and have broad visibility into…
Read More

“As a result of they function at this essential boundary, they usually maintain elevated privileges and have broad visibility into…
Read More
Apr 26, 2025Ravie LakshmananMalware / Vulnerability Cybersecurity researchers have detailed the actions of an preliminary entry dealer (IAB) dubbed ToyMaker…
Read More
Ukraine is exploring EU satellite tv for pc alternate options to Starlink, pushed by considerations over Elon Musk’s unpredictability. Starlink…
Read More
April 25, 2025 6 min watch Add matter to e mail alerts Obtain an e…
Read More
Cell community operator SK Telecom, which serves roughly 34 million subscribers in South Korea, has confirmed that it suffered a…
Read More
April 24, 2025 2 min watch Add matter to e mail alerts Obtain an e…
Read More
Kia has introduced that house owners of the EV6, EV9, and Niro EVs have formally gained entry to over 21,500…
Read More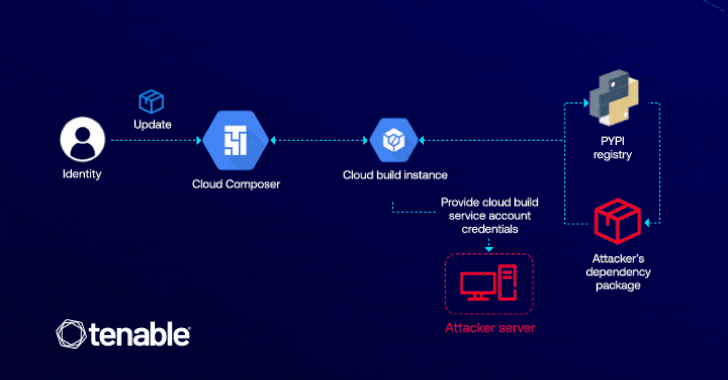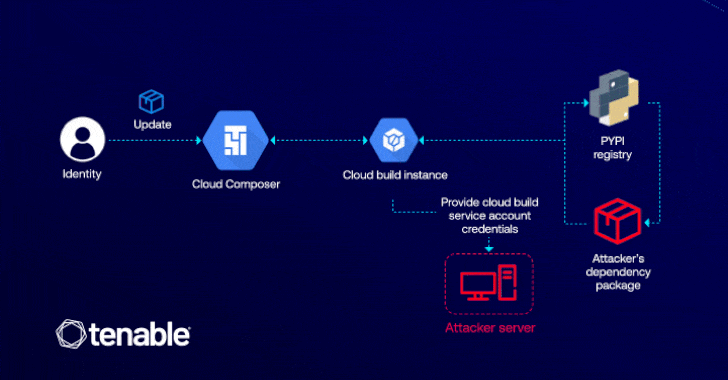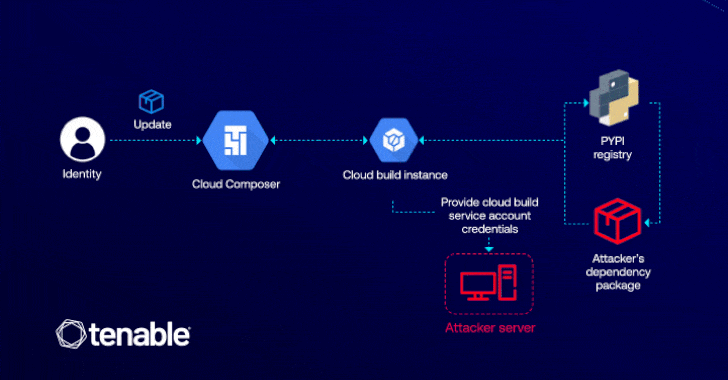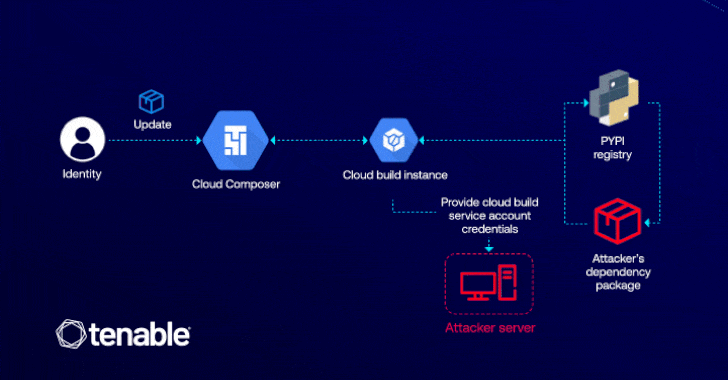
Cybersecurity researchers have detailed a now-patched vulnerability in Google Cloud Platform (GCP) that would have enabled an attacker to raise…
Read More