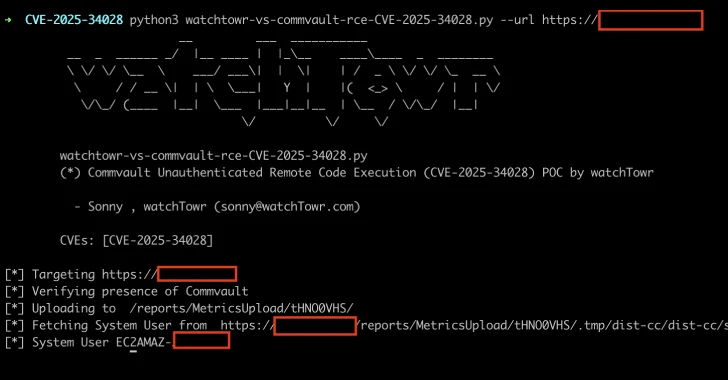
Menace actors are probably exploiting a brand new vulnerability in SAP NetWeaver to add JSP internet shells with the objective of facilitating unauthorized file uploads and code execution.
“The exploitation is probably going tied to both a beforehand disclosed vulnerability like CVE-2017-9844 or an unreported distant file inclusion (RFI) problem,” ReliaQuest mentioned in a report revealed this week.
The cybersecurity mentioned the opportunity of a zero-day stems from the truth that a number of of the impacted methods had been already working the most recent patches.
The flaw is assessed to be rooted within the “/developmentserver/metadatauploader” endpoint within the NetWeaver setting, enabling unknown menace actors to add malicious JSP-based internet shells within the “servlet_jsp/irj/root/” path for persistent distant entry and ship further payloads.
Put in a different way, the light-weight JSP internet shell is configured to add unauthorized recordsdata, allow entrenched management over the contaminated hosts, execute distant code, and siphon delicate information.
Choose incidents have been noticed utilizing the Brute Ratel C4 post-exploitation framework, in addition to a well known method known as Heaven’s Gate to bypass endpoint protections.
No less than in a single case, the menace actors took a number of days to progress from profitable preliminary entry to follow-on exploitation, elevating the likelihood that the attacker could also be an preliminary entry dealer (IAB) that is acquiring and promoting entry to different menace teams on underground boards.
“Our investigation revealed a troubling sample, suggesting that adversaries are leveraging a recognized exploit and pairing it with a mixture of evolving strategies to maximise their influence,” ReliaQuest mentioned.
“SAP options are sometimes utilized by authorities businesses and enterprises, making them high-value targets for attackers. As SAP options are sometimes deployed on-premises, safety measures for these methods are left to customers; updates and patches that aren’t utilized promptly are more likely to expose these methods to better danger of compromise.”
Coincidentally, SAP has additionally launched an replace to deal with a most severity safety flaw (CVE-2025-31324, CVSS rating: 10.0) that an attacker might exploit to add arbitrary recordsdata.
“SAP NetWeaver Visible Composer Metadata Uploader isn’t protected with a correct authorization, permitting an unauthenticated agent to add probably malicious executable binaries that might severely hurt the host system,” an advisory for the vulnerability reads.
It is probably that CVE-2025-31324 refers back to the similar unreported safety defect provided that the previous additionally impacts the identical metadata uploader part. The Hacker Information has reached out to ReliaQuest for additional remark, and we’ll replace the story if we hear again.
The disclosure comes somewhat over a month after the U.S. Cybersecurity and Infrastructure Safety Company (CISA) warned of lively exploitation of one other high-severity NetWeaver flaw (CVE-2017-12637) that might enable an attacker to acquire delicate SAP configuration recordsdata.