A brand new safety difficulty is placing WordPress-powered web sites in danger. Hackers are abusing the “Should-Use” plugins (MU-plugins) characteristic to cover malicious code and preserve long-term entry on hacked web sites.
In earlier 2025, safety researchers at Sucuri observed cybercriminals utilizing the tactic, they usually say that it has been more and more used the approach within the months since.
In WordPress, MU-plugins are plugins which are robotically enabled on a WordPress-powered website and – as the outline suggests – should be used, and due to this fact cannot be deactivated by means of the WordPress admin interface.
These “must-use plugins” are situated in a particular listing referred to as, imaginatively sufficient, mu-plugins throughout the wp-content folder. In contrast to common WordPress plugins, they might not be listed alongside common plugins except the “should use” filter is chosen.
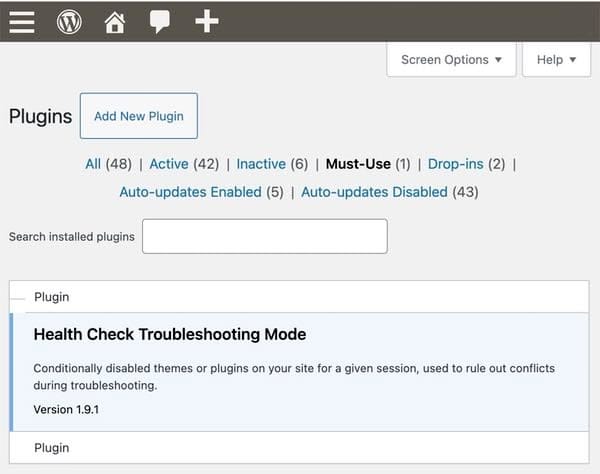
What makes a plugin “must-use”? Nicely, any plugin that’s important for the positioning’s performance and shouldn’t be turned off. This may increasingly embrace safety enhancements, efficiency optimisation, or multi-site administration options {that a} website’s builders or directors have deemed crucial to stay lively.
So there’s a good professional motive for a WordPress website to have “must-use” plugins, though many WordPress customers could also be largely oblivious to their existence.
In response to researchers, an assault sometimes begins when hackers compromise an internet site (typically through an out-of-date WordPress plugin, or weak password). As soon as an attacker has gained entry, they’ll plant a malicious PHP file into the mu-plugins folder, successfully giving it a persistent foothold on the web site.
Sucuri’s staff say they’ve seen three malicious MU-plugins being deployed in in-the-wild assaults:
- redirect.php – Sends web site guests to a bogus browser replace web page that downloads malware.
- index.php – A backdoor which grants attackers distant entry to the compromised server.
- custom-js-loader.php – Replaces web site content material with spam hyperlinks or specific photos.
These hidden mu-plugins run the hackers’ code on each web page of the web site, and might reinfect a complete website if nice care just isn’t taken to take away an an infection.
In an try and keep away from detection too quickly, the redirect plugin code avoids activating whether it is considered by one of many web site’s personal logged-in directors or a search engine bot.
After all, no one needs a hacker having a backdoor to their web site – granting an unauthorised get together admin-level management. A malicious attacker with such energy can steal information, create new admin accounts, or use your web site to unfold malware.
Moreover, you could discover any site visitors coming to your website is redirected by the malicious mu-plugins planted by the cybercriminals elsewhere on the web, doing hurt to what you are promoting and your model.
And it is dangerous information in your web site’s guests too. Anybody visiting an contaminated website is placing their pc susceptible to potential malware an infection.
The very best recommendation is to harden your WordPress website, by making certain that you simply use sturdy, distinctive passwords and have enabled two-factor authentication.
Moreover, monitor your website for uncommon behaviour, and guarantee which are conserving WordPress and any professional plugins and themes your web site makes use of correctly up to date.
Lastly, for those who suspect your WordPress-powered web site could possibly be internet hosting malicious MU-plugins, look within the wp-content/mu-plugins folder. Should you do not use MU-plugins it ought to be empty.